3 min read
New IIC Data Protection Best Practices: Securing complex IIoT systems by design, not luck
 Niheer Patel
:
July 25, 2019
Niheer Patel
:
July 25, 2019

A few days ago, the U.S. celebrated the 50th anniversary of the Apollo 11 crew landing on the moon, an incredible feat set in motion some eight years earlier, ultimately involving over 400,000 people working together to break barriers in space exploration and propel the country into the future.
As we fast forward to today, there are parallels between the original Moonshot and Industrial IoT. This time, it’s a race for data in unchartered territory. To win, there must be a collaborative effort to enable secure, reliable, scalable and intelligent data to run tomorrow’s industrial systems. As John F Kennedy said of the original Moonshot, we do these things “not because it is easy but because it is hard.”
IIoT data protection is hard indeed - a task and a mission that the Industrial Internet Consortium (IIC) takes very seriously. Over the past year, I had the pleasure of working on the new Data Protection Best Practices white paper, which supports the IIC’s goal of enabling the industry to build and secure scalable IIoT systems.
No one can deny the impact from the exponential proliferation of connected devices in Industrial IoT systems throughout the world. Over the next decade, we’ll see critical infrastructure and safety-critical OT systems connect with enterprise IT systems. This confluence will be a boon to disruptive business opportunities such as self-driving cars, distributed power grids, connected healthcare environments where preventable deaths are actually prevented, environmentally-friendly cities and much more.
This increased connectivity comes with increased risk of attack, as hackers seek to retrieve sensitive data or compromise the integrity of data to inflict harm to a business, property or worse, human lives. Check out my previous blog on autonomous vehicles for an example of the risks when data is compromised.
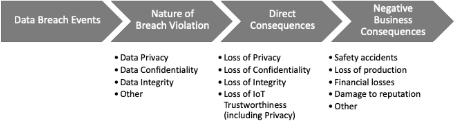
Figure 1—Data breaches can lead to multiple consequences [source IGnPower]
The new IIC white paper seeks to raise awareness that security is more than just a business problem. Security extends to a range of attributes that comprise what the IIC refers to as “IoT Trustworthiness”, which includes the safety of people directly impacted by these new technologies. The inherent complexity to IIoT security necessitates a team approach to tackling data protection.
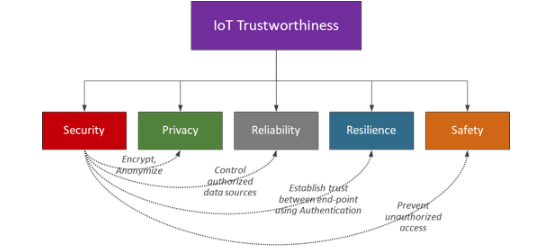
Figure 2—Data protection and the important role of Data security [source IGnPower]
Industrial IoT security has been widely debated by security experts over the past few years, with entire conferences covering the topic. So what’s the new information in the Data Protection Best Practices white paper?
Quite simply, the paper moves away from the ‘why’ to the ‘how’. It delivers a comprehensive roadmap for tackling data protection requirements, plans and architectural considerations early in the lifecycle of a new system.
How do you use this paper? While it can be read by itself, it is more impactful when used with the previously-published IIC Industrial Internet Security Framework. Start by identifying your business and technical motivations, so you can put the answers to “why does this matter?” in that framework. Review the Data Protection Best Practices paper with your key business and technical stakeholders to understand different categories of data protection, corresponding use cases and the risk of not applying the right kind of protective measure.
Short on time? We are too! We created red boxes to summarize the best practices for each category. These are quick references to get you thinking about the main concepts to consider within your IIoT system.
I’d like to give a special shout out to my co-authors, Bassam Zarkout of IGNPower and Apurva Mohan of Schlumberger - plus the input of the various IIC security groups - for their many hours of lively debate and discussions in gathering and sharing their expertise to share with the world.
Just as it took a team to build this white paper, it takes a team to protect data within an IIoT system. Our hope in writing this paper is to provide your organization with a comprehensive roadmap to ensure your security is built into your IIoT system, from the ground up.
About the Author
 Niheer Patel is the Product Manager for Aviation and Automotive Products at RTI, where he manages RTI’s high growth vertical product strategies to drive adoption of the RTI Connext platform in industry segments requiring high levels of modularity, autonomy, safety and security. He is responsible for safety certification efforts and driving security vision and execution for the Connext platform, especially as it pertains to safety-critical systems.
Niheer Patel is the Product Manager for Aviation and Automotive Products at RTI, where he manages RTI’s high growth vertical product strategies to drive adoption of the RTI Connext platform in industry segments requiring high levels of modularity, autonomy, safety and security. He is responsible for safety certification efforts and driving security vision and execution for the Connext platform, especially as it pertains to safety-critical systems.
In previous roles, Niheer led Wind River Systems safety certification efforts for VxWorks for IEC 61508 and in later roles served as product manager for the Wind River VxWorks 7 product line with a focus on security.
Posts by Tag
- Developers/Engineer (181)
- Technology (80)
- Connext Suite (77)
- News & Events (75)
- 2020 (54)
- Aerospace & Defense (54)
- Standards & Consortia (51)
- Automotive (38)
- 2023 (34)
- 2022 (29)
- IIoT (27)
- 2025 (25)
- Leadership (24)
- Healthcare (23)
- 2024 (22)
- Connectivity Technology (22)
- Cybersecurity (20)
- 2021 (18)
- Culture & Careers (15)
- Military Avionics (15)
- FACE (13)
- Connext Pro (10)
- JADC2 (10)
- ROS 2 (10)
- Connext Tools (7)
- Connext Micro (6)
- Databus (6)
- AI (5)
- Transportation (5)
- Case + Code (4)
- Connext (4)
- Connext Cert (4)
- Energy Systems (4)
- FACE Technical Standard (4)
- 2026 (3)
- Oil & Gas (3)
- RTI Labs (3)
- Research (3)
- Robotics (3)
- Connext Conference (2)
- Edge Computing (2)
- Golden Dome (2)
- MDO (2)
- MS&T (2)
- TSN (2)
- ABMS (1)
- C4ISR (1)
- DOD (1)
- Data Streaming (1)
- ISO 26262 (1)
- L3Harris (1)
- LabView (1)
- MOSA (1)
- MathWorks (1)
- National Instruments (1)
- Simulation (1)
- Tech Talks (1)
- UAM (1)
- Videos (1)
- eVTOL (1)
 Success-Plan Services
Success-Plan Services