5 min read
Become the Keymaster: Why You Should Use TPM with RTI Connext DDS Secure
 Fabrizio Bertocci
:
December 12, 2019
Fabrizio Bertocci
:
December 12, 2019

**Please note that with the April 2024 release of Connext Professional 7.3 LTS, the functionalities formerly comprising Connext Secure are now available as an optional component to Connext Professional, named Security Extensions.
Building secure systems and keeping them safe from increasingly sophisticated cyberattacks is a top challenge for developers. One way to combat this challenge is by using RTI Connext DDS Secure, the proven connectivity framework for building and securing complex distributed systems. Based on the DDS Security™ specification by the Object Management Group®, it provides robust, fine-grained security from device to cloud and everywhere in between. I wanted to share how using a Trusted Platform Module (TPM) device in conjunction with Connext DDS Secure makes a lot of sense for security-conscious developers.
First, a little background: When architecting a distributed system, the private identity of the individual nodes must of course be protected in order to ensure system security. So in configuring the system, developers need to determine the best way to distribute, store and protect the keys used to identify each node. While the common default of storing the keys on the node's persistent storage (hard disk, FLASH memory, etc.) may be convenient, it is certainly not very secure. In addition, many devices store information in an unencrypted manner, which also makes them susceptible to other types of attacks.
A Trusted Execution Environment (TEE) will protect the nodes (see our previous blog post on hardware security). However, TEEs are not widely available or widely used. In the absence of a TEE, the integrity of a DDS-based application cannot be guaranteed, as the same node might run rogue applications that could gain access to all the resources in a machine.
One solution to this problem is to store the identity key outside the node in a secure hardware device, where it cannot be physically accessed. In this approach, every cryptographic operation that requires access to the key must be implemented by the same hardware that protects the key. This is, after all, one of the main purposes of a TPM device.
TPM, also known as ISO/IEC 11889, is an international standard for a secure cryptoprocessor. This dedicated microcontroller authenticates hardware through integrated cryptographic keys. Each TPM chip contains an RSA key pair called the Endorsement Key (EK) that is maintained inside the chip and cannot be accessed by software.
There are two types of TPM chips: older chips that implement the TPM 1.2 specification, and newer versions based on TPM 2.0. While one of these variants is sometimes included on computer motherboards, the manufacturer does not always provide user access to them. So, you would need to do some investigation. TPMs are also available in other form factors, such as daughter cards.
Running a DDS Secure application that relies on the TPM (whether hardware or software) to protect the private keys of a node can significantly increase the security of a DDS-based system.
Putting the pieces together
The default RTI Connext DDS Secure Plug-in uses OpenSSL to perform every cryptographic operation. OpenSSL implements an ENGINE pluggable API in order to delegate some functionality to the appropriate hardware driver.
The following diagram shows how OpenSSL interfaces with a hardware device:
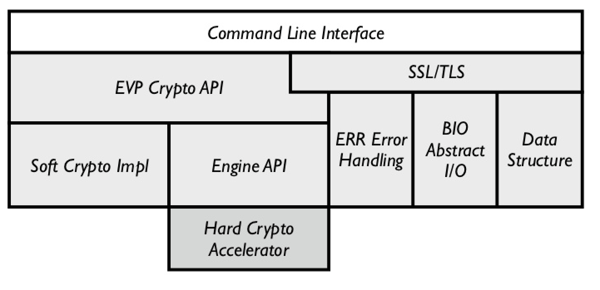
There are a few straight-forward steps required to configure DDS Secure to work with a TPM device:
- Ensure the system is able to identify and recognize the hardware TPM (low-level device driver).
- An OpenSSL ENGINE plug-in must be created or identified to delegate part of the cryptographic operations to the TPM (through the available driver API). Note: The default OpenSSL distribution does not include any support for TPM.
- The DDS Secure plugin must be configured to tell OpenSSL to use the specified engine.
1. System Support for TPM:
Operating system support for the TPM is dependent on the chip vendor. The modern version of Linux has a built-in kernel module available for several TPM vendors. Some embedded platforms might require additional support from the vendor in order to gain access to the TPM.
In RTI tests, we were able to successfully run DDS Secure applications using TPM (both 1.2 and 2.0) on Linux with a professional-grade laptop PC and a Raspberry PI. For the Raspberry PI, we used the Infineon Optiga SLB 9670 TPM with the device driver provided directly by Infineon. RTI users can access additional application notes that describe how to patch the Raspberry Pi Linux Kernel to add support for the Infineon TPMs.
2. OpenSSL Engines for TPM:
Open source support for TPM 1.2 is becoming quite obsolete. Most of the packages have not been upgraded in the last 5-6 years. Nevertheless, it is possible to build the current TrouSerS library and OpenSSL engine library (see OpenSSL TPM Engine sub-project) without too much effort.
In contrast, the open source support for TPM 2.0 is quite mature, with a rich set of tools and resources. The main TPM 2.0 project, is driven mostly by major hardware vendors. It contains several tools and libraries.
You can easily build tools and an OpenSSL engine for TPM 2.0 on any modern OS. Modern Linux kernels (newer than 4.14) also include a TPM resource management service, so you can easily share access to the physical TPM between multiple applications running on the same hardware. For older Linux versions, the open source community provides an Access Broker and Resource Manager daemon that interface with the dbus system to allow concurrent access to the TPM low-level driver from multiple applications.
3. DDS Secure Configuration:
Once you have a working hardware, driver and OpenSSL engine for the TPM, you can generate the private key used for the node identity through the TPM tools and OpenSSL command-line tool. Now you can generate the Certificate Signing Request (CSR). Have the TPM sign the CSR using the generated private key, and issue the identity certificate as usual. These steps are similar to the ones described in the getting started guide, with the exception of the key creation. Remember to specify the TPM engine through OpenSSL command-line using the -engine option. For example, to sign the CSR, use:
openssl req -engine tpm2tss -keyform engine -new -key
partATpmKey.keyblob -out partATpmCert.csr -config partATpmCert.conf
Note also that the -key parameter does not identify the real key, but instead a keyblob used to identify the internal private key (stored inside the TPM device).
At this point, when you have all the artifact files ready (keyblob, certificates, signed permissions and governance files) you can instruct DDS Secure to use the right OpenSSL engine and to load keys through the engine using the following properties:
- com.rti.serv.secure.library: specify the DDS Secure plug-in library that allows loading keys through the engine (see below)
- com.rti.serv.secure.openssl_engine: specify the TPM OpenSSL engine to use (tpm2tss for TPM 2.0)
- com.rti.serv.secure.authentication.keyform = "engine": tells the plugin to load the private key through the TPM and not from the file. The 'com.rti.serv.secure.authentication.private_key_file' now identifies the keyblob
- com.rti.serv.secure.authentication.private_key_file: points to the file containing the keyblob used to identify the private key
- [optional] com.rti.serv.secure.openssl_engine.tpm2tss.SET_TCTI: to assign the TCTI to use for the TPM communication (i.e. "tabrmd" or "device:/dev/tpmrm0")
- [optional] com.rti.serv.secure.openssl_engine.tpm2tss.SET_OWNERAUTH: to set the user's TPM password (if the parameters are preset)
The latest version of the RTI Connext DDS Secure plug-in directly supports loading the keys through the OpenSSL engine. Previous Connext versions require additional code changes. Please contact RTI support if you want to use TPM on an older version of RTI DDS Secure.
For additional information on using TPM with RTI Connext DDS Secure, please access my more detailed documentation:
- TPM 1.2:
https://community.rti.com/howto/using-tpm-12-dds-secure - TPM 2.0:
https://community.rti.com/howto/using-tpm-20-dds-secure
About the author
 Fabrizio Bertocci is a principal engineer at RTI. He has been with RTI for over 10 years. During his tenure, he has contributed to several parts of the RTI Connext DDS core libraries and products. He is currently with RTI Research, exploring new solutions, technologies and applications for DDS. Before joining RTI, he worked with EDA company Mentor Graphics, embedded silicon vendor VLSI (now NXP), along with technology start-ups. Fabrizio holds a Computer Engineering degree from the University of Pisa (Italy).
Fabrizio Bertocci is a principal engineer at RTI. He has been with RTI for over 10 years. During his tenure, he has contributed to several parts of the RTI Connext DDS core libraries and products. He is currently with RTI Research, exploring new solutions, technologies and applications for DDS. Before joining RTI, he worked with EDA company Mentor Graphics, embedded silicon vendor VLSI (now NXP), along with technology start-ups. Fabrizio holds a Computer Engineering degree from the University of Pisa (Italy).
Posts by Tag
- Developers/Engineer (181)
- Technology (80)
- Connext Suite (77)
- News & Events (75)
- 2020 (54)
- Aerospace & Defense (54)
- Standards & Consortia (51)
- Automotive (38)
- 2023 (34)
- 2022 (29)
- IIoT (27)
- 2025 (25)
- Leadership (24)
- Healthcare (23)
- 2024 (22)
- Connectivity Technology (22)
- Cybersecurity (20)
- 2021 (18)
- Culture & Careers (15)
- Military Avionics (15)
- FACE (13)
- Connext Pro (10)
- JADC2 (10)
- ROS 2 (10)
- Connext Tools (7)
- Connext Micro (6)
- Databus (6)
- AI (5)
- Transportation (5)
- Case + Code (4)
- Connext (4)
- Connext Cert (4)
- Energy Systems (4)
- FACE Technical Standard (4)
- 2026 (3)
- Oil & Gas (3)
- RTI Labs (3)
- Research (3)
- Robotics (3)
- Connext Conference (2)
- Edge Computing (2)
- Golden Dome (2)
- MDO (2)
- MS&T (2)
- TSN (2)
- ABMS (1)
- C4ISR (1)
- DOD (1)
- Data Streaming (1)
- ISO 26262 (1)
- L3Harris (1)
- LabView (1)
- MOSA (1)
- MathWorks (1)
- National Instruments (1)
- Simulation (1)
- Tech Talks (1)
- UAM (1)
- Videos (1)
- eVTOL (1)
 Success-Plan Services
Success-Plan Services